While the Angler Exploit Kit may have already established itself as one of the more sophisticated kits on the underground market, it appears it’s still finding ways to evolve.
Angler, this week, was spotted dropping the latest iteration of CryptoWall ransomware and leveraging yet another previously patched Adobe vulnerability.
Related Posts
POS Malware Nitlove Seen Spreading Through Spam Campaign
Adobe Unleashes Big Updates for Flash, Reader, Acrobat
Security Updates Coming for Adobe Reader, Acrobat
Earlier this year, the kit was spotted pushing a ransomware hybrid of sorts, a cross between TeslaCrypt and AlphaCrypt, along with a handful of Adobe exploits, and instances of the Bedep Trojan, which goes on to perpetrate click fraud.
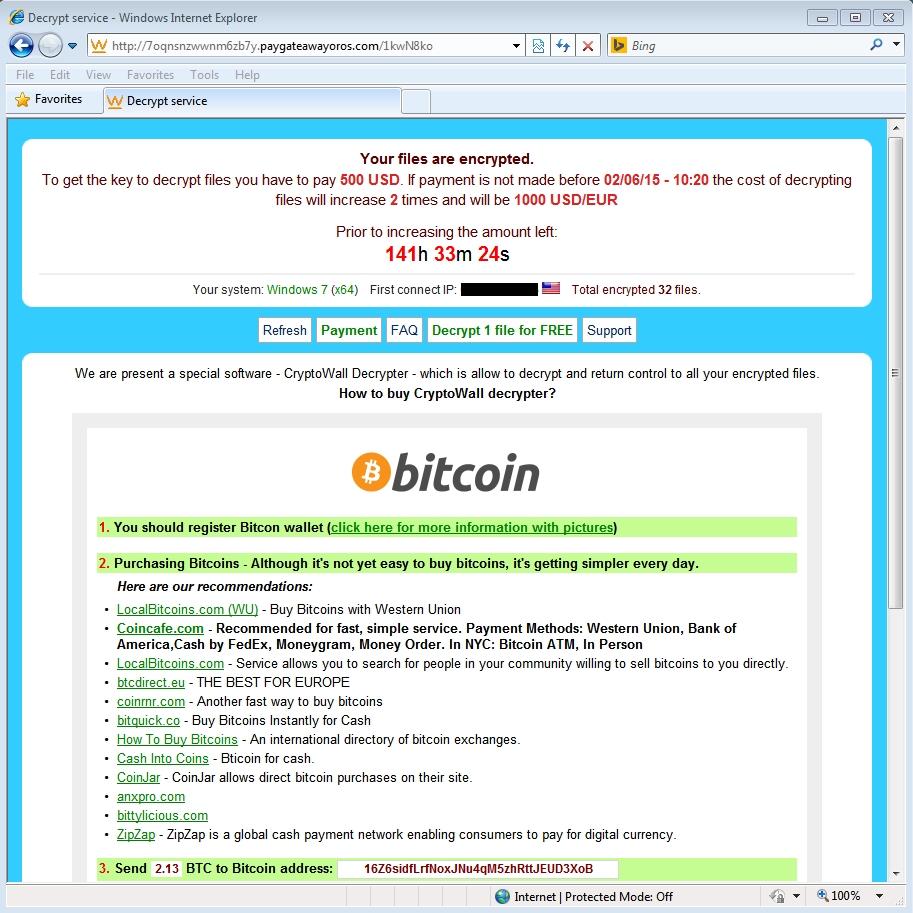
Brad Duncan, a handler at SANS Internet Storm Center claims he noticed two instances of Angler sending out Cryptowall 3.0 this week. In the first incident on Tuesday he spotted the kit dropping Bedep as a payload before it moved onto the CryptoWall 3.0. In a separate instance on Wednesday, he observed Angler sending Cryptowall 3.0 on its own.
Both times, Duncan claims, the ransomware used the same Bitcoin address for payment. Cryptowall also requested the usual figure, $500, to decrypt the victim’s files.
“I usually see Angler EK send different types of ransomware, and I’ve seen plenty of CryptoWall 3.0 samples from Magnitude EK; however, this is the first time I’ve noticed CryptoWall from Angler EK,” Duncan wrote in a post on SANS’ InfoSec Community Forums Thursday.
The exploit kit added yet another Adobe Flash Player vulnerability to its arsenal this week, according to FireEye. A quartet of researchers noticed Angler exploiting CVE-2015-3090 on Tuesday, about two weeks after Adobe actually patched the issue, a memory corruption vulnerability dug up by Chris Evans at Google’s Project Zero.
The kit uses the vulnerability to exploit a race condition in the shader class and trigger the vulnerability, making it possible for attackers to execute arbitrary code and infect the systems of users who haven’t updated yet.
The addition of Adobe exploits to Angler certainly isn’t new by any means but as FireEye points out, it is worrisome.
In January the kit added two Flash vulnerabilities, including a zero day that went onto install Bedep on victims’ machines. In April the kit began exploiting CVE-2015-0359 in Flash and in March it narrowed its sights on CVE-2015-0336, also in Flash, along with an IE vulnerability.
The kit matured further in March, adding a nifty trick called domain shadowing wherein pilfered domain credentials are used to build lists of subdomains and then used to redirect victims to attack sites.
Provided from: Techcrunch.