Kaspersky Lab researchers say that a recent analysis of two Backoff malware command and control servers paints “a very bleak picture of the state of point-of-sale security.”
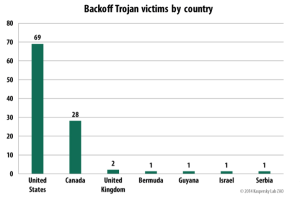
Kaspersky Lab sinkholed two of the malware’s command and control servers. In just two days, nearly 100 infected systems, mostly in the U.S. and Canada but also in a number of other countries, attempted to contact the servers which are now no longer controlled by Backoff’s authors. Victims are said to include a popular Mexican restaurant chain in the U.S., a North American freight shipping and transport logistics company, a liquor store chain in the U.S., a North American payroll association and more.
Related Posts
Secret Service Warns 1,000 Businesses Hit by Backoff PoS Malware
New Backoff PoS Malware Identified in Several Attacks
Brute-Forcing Botnet Sniffs Out Lax POS Systems
“Our sinkhole covers less than 5 percent of the C&C channels and the sinkholed domains only apply to certain Backoff samples that were created in the first quarter of this year,” says the Kaspersky Lab Global Research and Analysis Team. “Yet, we’ve seen more than 85 victims connecting to our sinkhole.”
Researchers estimate that there are more than 1,000 infection in the U.S.
Backoff is a piece of malware that targets the point-of-sale terminals that process payment information at retail locations. This year has been something of a golden age for such malware. Breaches at Target and Michael’s are known to have been caused by point-of-sale malware, and breaches of customer payment data at various other locations like the Albertson’s and Supervalu grocery store conglomerates, UPS, and others are all but confirmed to have been caused by point-of-sale malware as well.
In the past year, we’ve written about at least four different point-of-sale threats: Chewbacca, Dexter, a class of malware known as RAM scrapers and now Backoff.
Furthermore, security firm Arbor Networks released a report earlier this year noting that point-of-sale systems are poorly secured and facing sophisticated attacks. Lucas Zaichowsky, enterprise defense architect at AccessData, doubled down on this sentiment in a briefing at the Black Hat security conference earlier this month. However, the Verizon Data Breach report actually suggested that point-of-sale malware is trending downward, despite what headlines would have you believe.
“It’s very clear that PoS networks are prime targets for malware attacks,” Costin Raiu, Ryan Naraine and Roel Schouwenberg wrote in a Securelist analysis. “This is especially true in the US, which still doesn’t support EMV chip-enabled cards. Unlike magnetic strips, EMV chips on credit cards can’t be easily cloned, making them more resilient. Unfortunately, the US is adopting chip and signature, rather than chip and PIN. This effectively negates some of the added security EMV can bring.”
Provided from: threatpost.