And another password shocker, a few days after ‘cloud’ password service LastPass was pretty seriously hacked (yah if you’re using it, change your master password) critical 0-day flaws in Apple’s password storing keychain have been exposed.
Which is kinda funny, as after the LastPass hack I saw some people espousing the usage of Apple’s keychain as much more secure. And now, Apple’s keychain cracked – and in a really serious way.
Six university researchers have revealed deadly zero-day flaws in Apple’s iOS and OS X, claiming it is possible to crack Apple’s password-storing keychain, break app sandboxes, and bypass its App Store security checks.
Attackers can steal passwords from installed apps, including the native email client, without being detected, by exploiting these bugs.
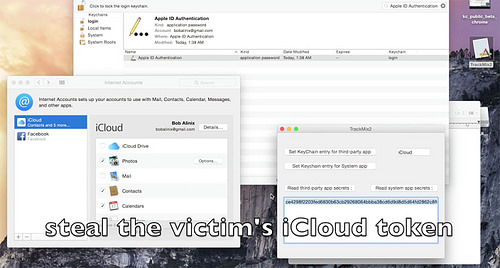
The team was able to upload malware to the Apple app store, passing the vetting process without triggering alerts. That malware, when installed on a victim’s device, raided the keychain to steal passwords for services including iCloud and the Mail app, and all those stored within Google Chrome.
Lead researcher Luyi Xing told El Reg he and his team complied with Apple’s request to withhold publication of the research for six months, but had not heard back as of the time of writing.
They say the holes are still present in Apple’s software, meaning their work will likely be consumed by attackers looking to weaponize the work.
Apple was not available for immediate comment.
It’s pretty serious as they managed to bypass the app store vetting and can grab access tokens and data from other apps on the device including high profile apps like Facebook, Evernote and iCloud itself even while sandboxed.
The sad part is, Apple was notified about this 6 months ago and still haven’t fixed it – the only fast moving response came from Google’s Chromium security team who removed keychain integration for Chrome, noting that it could likely not be solved at the application level.
“Recently we discovered a set of surprising security vulnerabilities in Apple’s Mac OS and iOS that allows a malicious app to gain unauthorised access to other apps’ sensitive data such as passwords and tokens for iCloud, Mail app and all web passwords stored by Google Chrome,” Xing told The Register’s security desk.
“Our malicious apps successfully went through Apple’s vetting process and was published on Apple’s Mac app store and iOS app store.
“We completely cracked the keychain service – used to store passwords and other credentials for different Apple apps – and sandbox containers on OS X, and also identified new weaknesses within the inter-app communication mechanisms on OS X and iOS which can be used to steal confidential data from Evernote, Facebook and other high-profile apps.”
The team was able to raid banking credentials from Google Chrome on the latest OS X 10.10.3, using a sandboxed app to steal the system’s keychain data and secret iCloud tokens, and passwords from password vaults.
If any malicious teams are out there using this, it could be really bad – and well if they aren’t already using it my bet is they will be by tomorrow.
I guess it’ll probably be blocked from the app store by then though, now it’s getting widespread media coverage.
You can read the full report, including in-depth technical details here – Unauthorized Cross-App Resource Access on MAC OS X and iOS
Source: The Register
Provided from: Techcrunch.